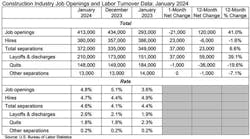
Companies must decide what IT products to buy (hardware and software), how to track those devices and their licenses, how and when to service them, what to do if one of their IT assets goes missing or comes under attack, and more.
“The Target debacle triggered an 8% increase in spending on ‘IT security’ but did very little to slow down the tide of major data breaches," Rembiesa says. "The reality is that companies that have taken these steps are treating the symptoms but not the underlying problems. By focusing only on narrowly focused and superficial IT security ‘solutions,’ companies are putting the cart before the horse and they’re going nowhere.”
RELATED ARTICLES:
Combating the Evolving Malware Threat
Protecting Data Centers from Mechanical Failure
She adds: “When you look closely at the biggest data breaches of 2014, even the best IT security solutions alone could never prevent them. This has been the biggest ignored lesson of the year. If companies are to stop these attacks in 2015, they must first recognize that the true source of nearly all major breaches are more foundational and stem from nonexistent or inadequate IT Asset Management procedures.”
Dr. Rembiesa urges companies intent on more fully protecting themselves from data breaches to consider several key IT Asset Management principles:
- You Can't Secure What You Don’t Know You Have. One of the greatest breach risks to all enterprises lies in the large number of IT doorways and gateways. No amount of sophisticated security software on earth will protect a company from the computer it didn’t know it had operating on its network, or the dangerous software that was downloaded by an employee on an undetected basis. Companies must know and actively manage what is in their IT environment if they are to secure it. In 2014, a case study on the dangers of mismanaging IT hardware was seen at Coca-Cola, which revealed that an employee had, without detection, stolen 55 laptops over a six-year period. Those laptops, Coca-Cola later acknowledged, contained tens of thousands of social security numbers and other sensitive data.
Communications management accelerates the speed at which a discovered threat can be locked down and addressed.
Focusing on IT security without addressing IT Asset Management may provide some degree of comfort in board rooms and C suites looking for a quick fix, but it is an illusion.
- Information technology environments operate in dynamic and fluid ways, and IT Asset Management is the discipline that helps companies navigate and understand this process. Focusing on IT security without addressing IT Asset Management may provide some degree of comfort in board rooms and C suites looking for a quick fix, but it is an illusion. A recent example of how a breakdown in IT Asset Management could thwart the best IT security policies occurred at the National Health Service (NHS) of the United Kingdom. A significant data breach took place there after an NHS IT vendor sold several hard drives on EBay instead of destroying them, as instructed. Highly sensitive information on tens of thousands of patients ended up in the hands of the purchasers of the drives. If proper IT Asset Management procedures were followed, this type of vendor mismanagement would never occur: the drives would have been thoroughly wiped before ever being sold, and only certified IT Destruction vendors would have been contracted for the actual hard drive disposal.
Rembiesa points out that most companies face on a daily basis a range of critical IT decisions. They need to decide what IT products to buy (hardware and software), how to track those devices and their licenses, how and when to service them, what to do if one of their IT assets goes missing or comes under attack, and more. Mishandling or misappropriating at any key IT junctures exposes companies to data breach risk.
Rembiesa noted: “It is critical to have IT Asset Managers that are certifiably up to speed on best IT Asset Management practices, and in the 2014 data breach deluge, this has been the glaring gap. Until companies do more to support their IT security operations with proper and effective IT Asset Management, you can expect data breaches to continue largely unabated.”